Confidential Computing is a cloud-based technology aimed at enhancing the security and privacy of data during data processing (i.e., data in-use) using hardware-based trusted execution environments. Typically, in software application, data journeys through three different states: at-rest, in-transit, and in-use. When data is at rest (i.e., when data is stored in a database or saved as a file to hard drive), it follows standard encryption practices to secure the stored data. Similarly, when data is in-transit (i.e., when data moves across the network), industry standard network security protocols are employed to secure the communication channel of the transmitted data. However, when data is in-use (i.e., when data is processed or analyzed in server memory), it is in an unprotected form and open to potential memory attacks and data exposure.
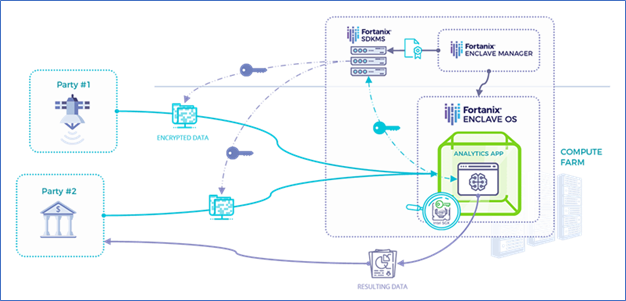
Confidential Computing eliminates the risk of data exposure during the in-use state by providing a trusted execution environment (TEE). The TEE or “secure enclave” is formed on the server by hardware-level encryption that isolates a portion of the server and its resources to create a trusted/secure environment/enclave that protects and prevents unauthorized access to all that it encompasses (i.e., code and data). Essentially, Confidential Computing creates a hardware boundary within the server that prevents anyone with access to the server, whether malicious or not, from accessing anything within the boundary. It provides an additional layer of protection and encryption within the server itself, so if the infrastructure is compromised where the server is deployed, all code and data within the secure enclave will still be protected.
Confidential Computing successfully protects data in-use, but by creating a hardware-based encrypted boundary within the server it essentially creates a black box where one cannot determine from the outside what is occurring on the inside. This lack of transparency requires a mechanism for system users to be confident that the code/application executing inside the boundary has not been tampered with. The Confidential Computing architecture introduces the concept of Attestation as the solution to this problem. Attestation cryptographically generates a hash of the code or application approved for execution in the secure enclave, and this hash is checked every time before the application is run in the enclave to ensure its integrity. The attestation process is a necessary component of the Confidential Computing architecture and works together with the TEE to protect data in all three states.
Confidential computing is an enterprise-owned infrastructure solution that requires specialized hardware. It can handle complex workloads with large amounts of data normally seen in data analytics and machine learning. In addition to data privacy, secure processing, and protection from insider threats, it enables secure collaboration and data sharing among multiple parties, even if they don’t trust each other. In the growing field of privacy enhancing technologies, Confidential Computing is destined to become another layer of security that the major cloud providers will look to assimilate into their platforms. It shows potential in the healthcare industry for safeguarding sensitive health data, empowering healthcare organizations to be data-driven and collaborative while upholding the highest standards of data confidentiality.
Fortnaix’s Illustration of Confidential Computing Architecture
Source: https://www.fortanix.com/blog/confidential-computing-the-early-bird-catches-the-worm

